Card reader
Punkty: 500
Rozwiązań: 3
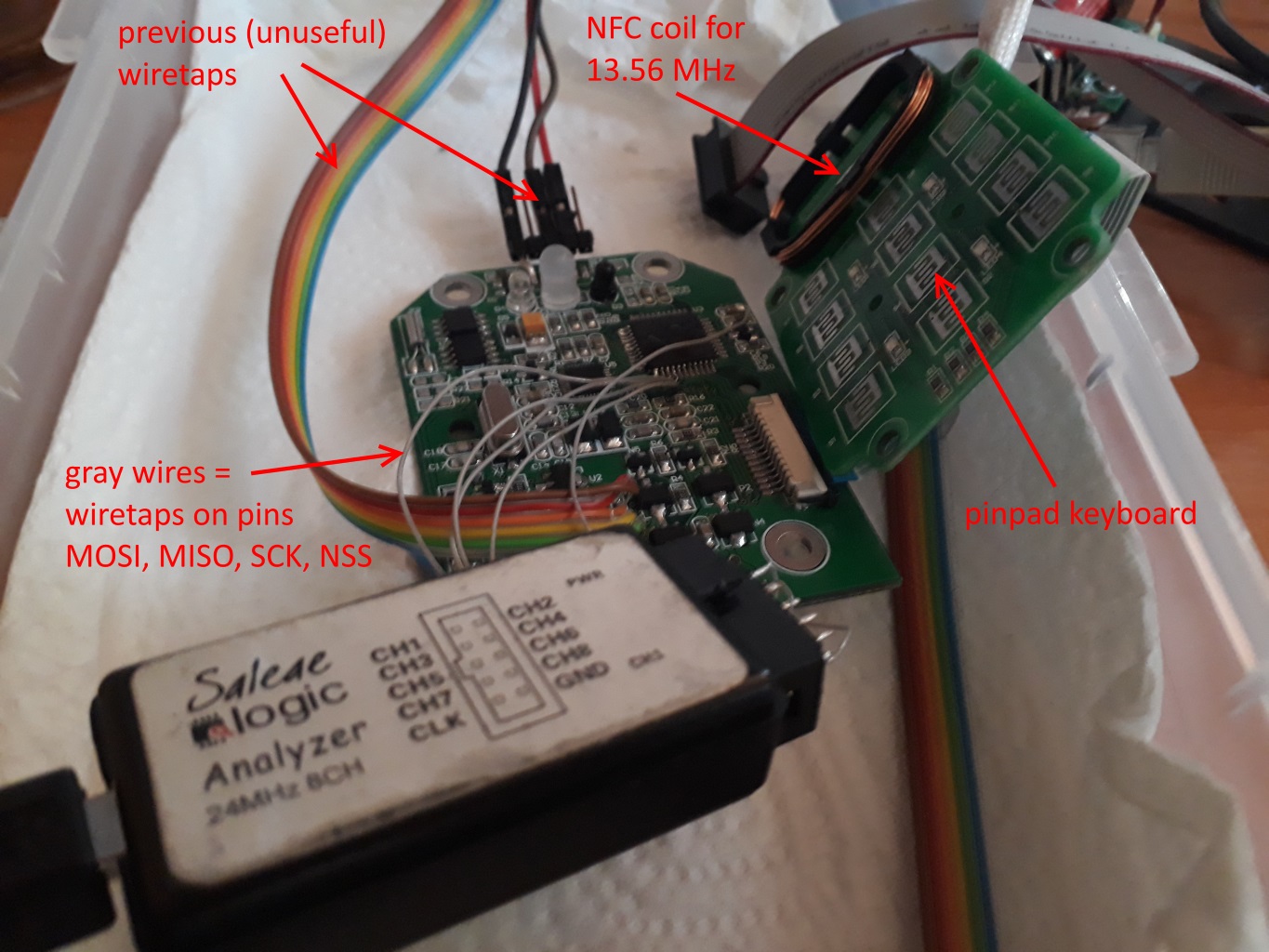
We need to reverse-engineer a card reader which looks similiar to this one:
On the mainboard, there is an Atmega164PA-AU microprocessor along with (probably?) MFRC522 device (also called NFC frontend). We know that cryptography is done on the microprocessor, so we've wiretapped the SPI communication interface between these two chips:
In
captureX.logicdatafiles there are recordings of what happens on this SPI interface when correct card is presented to the reader. We've also managed to steal unstripped binary of microprocessor's firmware.The communication is probably encrypted and cards used are Mifare DESFire EV1 model. For the recorded communication the card UID was
04:18:75:FA:11:4E:80.Could you help us decipher recorded communication?
Hint 1: I found some assets on the Internet, may be helpful: DESFire Communication Examples.
Hint 2: Somebody found out how DES/CBC mode works in DESFire.
Format flagi:
ecsc{litery_cyfry_i_znaki_specjalne}.